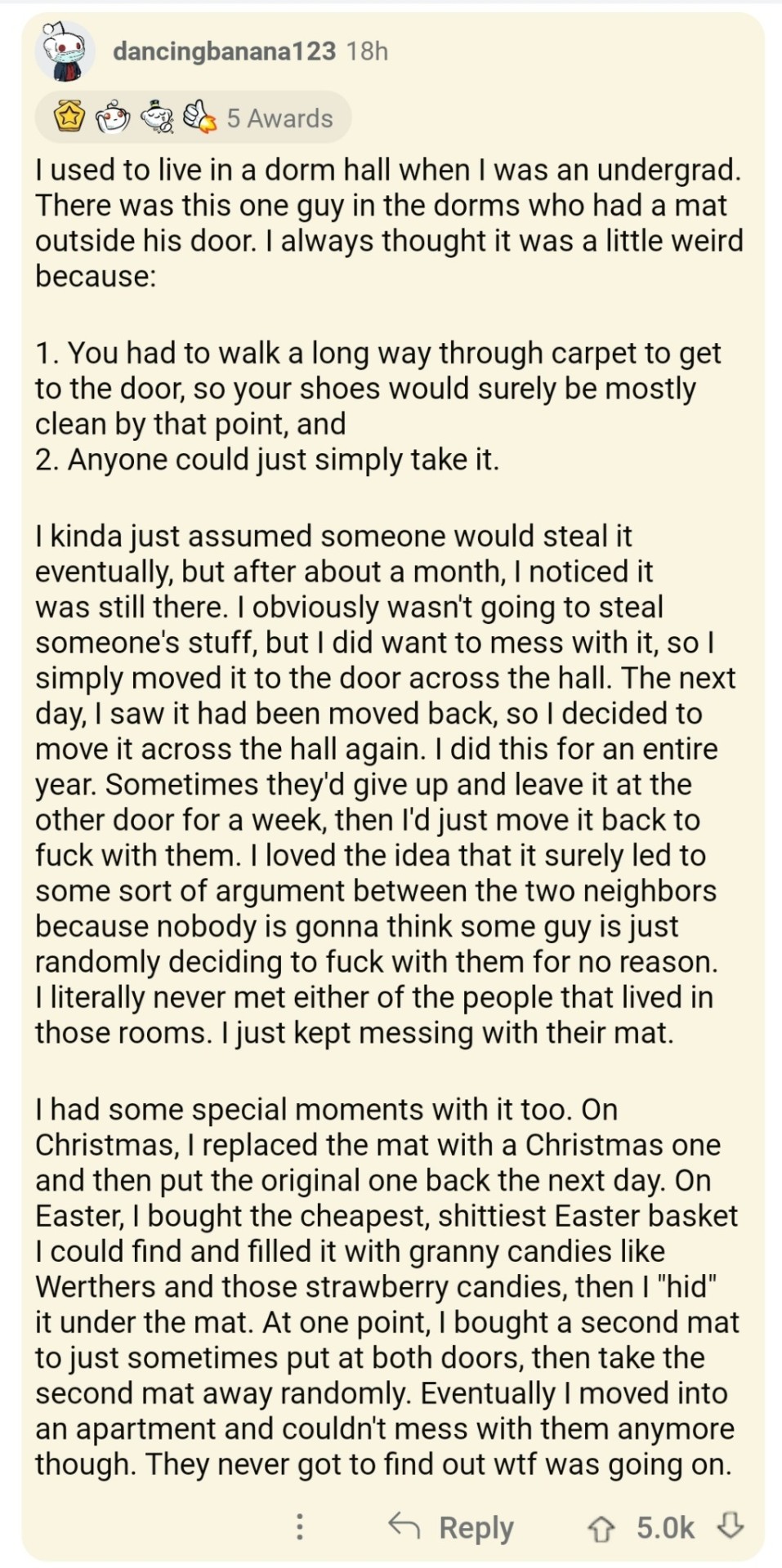
Reblog To Teleport Your Mutuals To A Massive Party When Jkr Dies
reblog to teleport your mutuals to a massive party when jkr dies
More Posts from Silliestofmanygeeses and Others

the world is healing
please learn how to code
like, if you're bored today, and not doing anything,
learn a little bit of coding please
Well since you all asked nicely...
Time you all learn how to get into being a hacker~!
Advance warning this will be a long post and as of typing this idk if tumblr has char limits so might need to continue in reblogs?
Right, so. You may be asking "How do I get into hacking?" and find yourself here because of it.
The answer is you just did it. Right there. By clicking that keep reading link you have just entered the world of hacking, because curiosity is everything. The innate urge to learn more, to know more, that is what hacking comes down to. You do more than just using a system, you question it. Ask yourself, what does the system do when i input these characters? How does it take my input and translate it into the function? Where does it store information in what way?
Have you ever tried inputting unexpected text into a field? For example, say a website asks for a particular input like your name, but instead you start putting in numbers or unexpected unicode. That right there is, by definition, the poking around that hacking uses. You're experimenting with unexpected use-cases. Often times if you try this, you may end up finding interesting results. In my example here, say instead of your name, you put ../../../../etc/passwd into the field. Suddenly when you hit enter, you get hit with a result of a bunch of names and data. That is a hack. The database to control the storage of your name instead received a command to back out of that database, and go into the etc folder to retrieve the passwd folder, which houses user data from that system. This, of course, assumes the system is running Linux, but it is an example. All hacking is, is poking around in ways the original programmer couldn't expect to find interesting results and broaden your access into things you shouldn't have.
Now, this is all well and good, but what if you want an actual way to learn this in person? Well the good news is there are plenty of legal avenues to get into hacking and broaden your experience! Personally I use HackTheBox for my CTFs through their labs. That means they run a thing called Capture The Flag, where they give you a single IP and you have to explore that system to find two different flag files to win. They also have competitive CTFs I have yet to try, but I do have a competitive tournament coming up next month for it. Then they also have the academy to teach you more via both hands-on methods and reading work. If you know next to nothing and want to get started in a safe learning environment, you can try out their academy or my next resource. TryHackMe! This website is more learning focused, and I have been taught a lot of what I know through it! It has free lessons along with premium ones for a subscription, so just know that only a selection of what you can learn here is free, but I do recommend them if you do feel like paying for that extra bit, as I would say what I learned from it was worth it and they focus on both offensive hacking, which I do, as well as the blue side for defensive hacking and even things like digital forensics if you're interested in that!
HackThisSite. No really, hack it! This website is a legal playground to try out scenarios from the unlikely to the realistic in varying difficulties to put your skills to the test!
There's many, many more resources to look into as well, those are just the first few off the top of my head. Beyond this, I'd say constantly stay up to date in cybersecurity news and read up on new large scale attacks, as the entire industry is a constant arms race with exciting twists to learn about! Beyond that there is no one right way to go about hacking, and there's never a stupid idea to it either!
Now, all this is well and good, but what about a real case example? Well luckily for you all I happen to have a machine up and running to show off a case example of a CTF in action. Today i'll be showing you the "Lame" box from HackTheBox, the first machine they ever published, now retired. I can access it thanks to VIP.
First thing's first, I'm using a laptop that I stripped of Windows 11 in favor of Linux, and specifically Kali Linux being the exact distro. If you're wanting to get into hacking at the VERY least use a VM with linux, but i beg of you dont use windows. You're asking for trouble both in terms of lack of tools and in terms of vulnerability. You're putting a VERY large target on your back by using Windows because of how vulnerable it is. Kali Linux is a nice option as it comes pre-built with tools, but if you want something more user friendly you can go for Parrot OS.
Once the OpenVPN connection is active and we have the Lame machine up and running, it gives us an IP and nothing more. The first thing you will want to do when this is the case is to use a tool called Nmap to scan that IP for active TCP ports. This shows you what open, and sometimes closed, connections that machine is running, along with information about them. I usually use the command with these particular flags. nmap -sV -Pn -p- (ip)

It will output the ports we want to see, dont worry about how much text there is, we're focusing on just a small segment saying port numbers and a description of them

Now that's interesting, looks like this is running Samba SMBD on ports 139 and 445, and thanks to a google search I know this is a vulnerable version. We'll take the quick route and just use a tool called Metasploit. In a typical run metasploit wont have what you need, but for the sake of time and post length, i'll just boot that up by running "msfconsole" and running a search for our exploit. On finding the one I need I select the payload.

Next up, we need to equip the options for it, setting who our target is and where to send the information back to, in this case my VPN's IP.

Once that's done, you simply say "run" and it will go! And what do you know, i'm in the system as a root user, aka full administrative privileges with access to both the user and root flag! In a typical CTF there are many more steps including usually getting into the user first, then exploiting into root. I, however, took the shorter route this time.

(The flags change every run so you cant just copy paste them from my run.)
And that's that, machine conquered! We did it! Of course, in the real world of hacking there are many more steps, and it can even take multiple days to get everything you need from a target in a stealthy manner. The faster you move, the louder you are.
Now you know the basics though! Get out there and learn, google will be your friend and its never wrong to ask questions. My DMs are open if you have more to ask or just wanna talk hacking! :3
Legal, illegal, who cares im not a cop, have fun and stay curious~!
reblog if you think sign language should be taught as a language in schools.
🗣🗣🗣🗣🗣
on a list of dumb shit i know:
the grass in the original shrek movie is not grass. its hair. they used hair textures for the grass bc the actual grass for some reason in their computer modelling programs would not behave like grass so they used hair textures colored green.
i hate that fucking right-wing nudniks have ruined these topics for us but if you ever see a meme or funny post and the subject is like, ancient rome, medieval europe, military stuff, or guns, check the OP before reblogging. Half the time it turns out to be some brand of fash and 30 seconds of scrolling on their blog will find some racist shit or something similarly hateful
please report any hate speech you find and block them. bonus is that their chud buddies are usually reblogging the OP too so you get a free report/block list

In love with this
Ahhh thank you!!
In music you have major keys and minor keys and these keys have a set of pitch collections that make up different chords. These chords make up different sounds such as major chords and minor chords. Major chords are your happy sounding chords (if you know solfege its do-mi-sol) and minor chords are your sadder sounding chords (think la-do-mi)
In both major and minor keys, the 1 chord will always be seen as the “home” chord (if the song feels resolved it ends on the 1 chord).
Because a lot of chord structures are similar, on of the ways musicians make a short hand of these chords is by using roman numerals. When the song is in a major key, the roman numeral I (“uppercase 1”) is used to notate it and in a minor key its i (“lowercase 1”). This is to easily show other musicians what variation of the chord is being played and makes reading sheet music easier.
(I hope this all makes sense im typing this all on my phone rn. If you need clarification please ask.) (It also helps that i am a music major in college so i kinda need to know this to not fail lmao)
i is such a cool number. I wish it was real

-
 mad-willleo10 liked this · 1 month ago
mad-willleo10 liked this · 1 month ago -
 tilescel reblogged this · 1 month ago
tilescel reblogged this · 1 month ago -
 yuviagamer reblogged this · 1 month ago
yuviagamer reblogged this · 1 month ago -
 fatiguedrodent reblogged this · 1 month ago
fatiguedrodent reblogged this · 1 month ago -
 fatiguedrodent liked this · 1 month ago
fatiguedrodent liked this · 1 month ago -
 psychedelicflyingshark reblogged this · 1 month ago
psychedelicflyingshark reblogged this · 1 month ago -
 youvegot-timetogrow reblogged this · 1 month ago
youvegot-timetogrow reblogged this · 1 month ago -
 entitledcrayonscribbler reblogged this · 1 month ago
entitledcrayonscribbler reblogged this · 1 month ago -
 entitledcrayonscribbler liked this · 1 month ago
entitledcrayonscribbler liked this · 1 month ago -
 coughingoutembers liked this · 1 month ago
coughingoutembers liked this · 1 month ago -
 drakesteardrop reblogged this · 1 month ago
drakesteardrop reblogged this · 1 month ago -
 drakesteardrop liked this · 1 month ago
drakesteardrop liked this · 1 month ago -
 the-inconceivable-glue-man reblogged this · 1 month ago
the-inconceivable-glue-man reblogged this · 1 month ago -
 the-inconceivable-glue-man liked this · 1 month ago
the-inconceivable-glue-man liked this · 1 month ago -
 purpleduder reblogged this · 1 month ago
purpleduder reblogged this · 1 month ago -
 seabirdsong liked this · 1 month ago
seabirdsong liked this · 1 month ago -
 unfortunatelystuckhere reblogged this · 1 month ago
unfortunatelystuckhere reblogged this · 1 month ago -
 unfortunatelystuckhere liked this · 1 month ago
unfortunatelystuckhere liked this · 1 month ago -
 meow-nir reblogged this · 1 month ago
meow-nir reblogged this · 1 month ago -
 daesha09thenumberonewolflover reblogged this · 1 month ago
daesha09thenumberonewolflover reblogged this · 1 month ago -
 soft-blankets108 reblogged this · 1 month ago
soft-blankets108 reblogged this · 1 month ago -
 astralfuchs reblogged this · 1 month ago
astralfuchs reblogged this · 1 month ago -
 astralfuchs liked this · 1 month ago
astralfuchs liked this · 1 month ago -
 ferret-propaganda liked this · 1 month ago
ferret-propaganda liked this · 1 month ago -
 zouex reblogged this · 1 month ago
zouex reblogged this · 1 month ago -
 rhymeswithjellyfish liked this · 1 month ago
rhymeswithjellyfish liked this · 1 month ago -
 fistmyholes reblogged this · 1 month ago
fistmyholes reblogged this · 1 month ago -
 jakevrakng liked this · 1 month ago
jakevrakng liked this · 1 month ago -
 stellewriites reblogged this · 1 month ago
stellewriites reblogged this · 1 month ago -
 oblivdova reblogged this · 1 month ago
oblivdova reblogged this · 1 month ago -
 oblivdova liked this · 1 month ago
oblivdova liked this · 1 month ago -
 spitefulmercy reblogged this · 1 month ago
spitefulmercy reblogged this · 1 month ago -
 pyrose-the-flame reblogged this · 1 month ago
pyrose-the-flame reblogged this · 1 month ago -
 crazyw3irdo reblogged this · 1 month ago
crazyw3irdo reblogged this · 1 month ago -
 newborthdaysong liked this · 1 month ago
newborthdaysong liked this · 1 month ago -
 silver-heller liked this · 1 month ago
silver-heller liked this · 1 month ago -
 nyxmahogany reblogged this · 1 month ago
nyxmahogany reblogged this · 1 month ago -
 nyxmahogany liked this · 1 month ago
nyxmahogany liked this · 1 month ago -
 jonathanrook reblogged this · 1 month ago
jonathanrook reblogged this · 1 month ago -
 foxinpox liked this · 1 month ago
foxinpox liked this · 1 month ago -
 drowsyinsomnia reblogged this · 1 month ago
drowsyinsomnia reblogged this · 1 month ago -
 wafflessart liked this · 1 month ago
wafflessart liked this · 1 month ago -
 eternighost reblogged this · 1 month ago
eternighost reblogged this · 1 month ago -
 eternighost liked this · 1 month ago
eternighost liked this · 1 month ago -
 rustyshiv reblogged this · 1 month ago
rustyshiv reblogged this · 1 month ago -
 rustyshiv reblogged this · 1 month ago
rustyshiv reblogged this · 1 month ago -
 rustyshiv reblogged this · 1 month ago
rustyshiv reblogged this · 1 month ago -
 rustyshiv reblogged this · 1 month ago
rustyshiv reblogged this · 1 month ago -
 rustyshiv reblogged this · 1 month ago
rustyshiv reblogged this · 1 month ago -
 avas-queen-black liked this · 1 month ago
avas-queen-black liked this · 1 month ago

I’m not a bot, I just kinda like to browse and exist here occasionally :))))
193 posts